
What happens when legislatures pass laws enabling law enforcement to obtain sensitive, private information about people without requiring any evidence of criminal activity, and without any outside oversight whatsoever?
Fishing expeditions.
Take a look at this graph, produced by US Cellular in response to Senator Ed Markey's letters to cell phone companies seeking information about law enforcement surveillance requests.
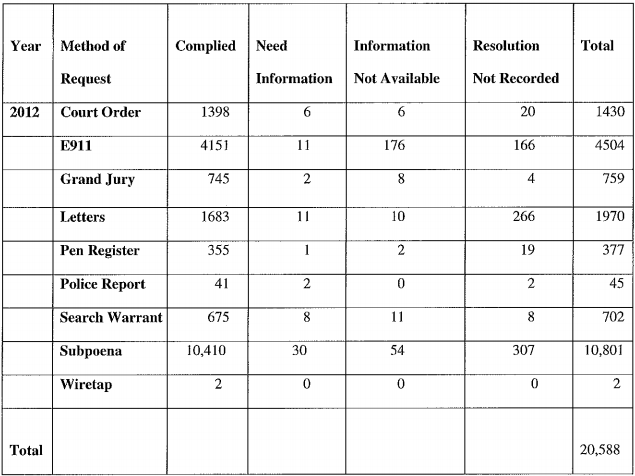
Note that the company only received 2 wiretap orders in 2012. Wiretap statutes require judicial oversight and for law enforcement to produce sworn statements affirming that the search will likely result in evidence of a specific crime -- probable cause. Some wiretap statutes are even stricter, requiring that the crime under investigation be very serious, like racketeering or murder. Search warrants require probable cause affirmations and judicial approval, too. Law enforcement submitted only 702 search warrants to US Cellular in 2012.
On the other hand, the company received 10,801 subpoenas in 2012. Unlike wiretap orders and search warrants, subpoenas require zero judicial oversight nor probable cause. In fact, a prosecutor can issue a subpoena even absent any allegation that the subject of the surveillance is connected to criminal activity. The requirement is simply that the subpoena have something to do with (in legal parlance is "relevant" to) an ongoing investigation.
That means any prosecutor -- yes, including the prosecutors at your local district attorney's office -- can simply fill out a form (a subpoena) and send it to a cell phone company, demanding personal information about anyone. In many states, including Massachusetts, there is zero outside oversight to ensure that law enforcement doesn't abuse this broad power. We don't even know how many of these subpoenas are issued every year. When we asked district attorneys in Massachusetts, many of them said they don't keep records of how many they file. But we know it's common enough that the system is abused. In 2013, the Middlesex county DA's office got into some hot water when it was discovered that a secretary was illegally issuing the subpoenas, which are supposed to come only from DAs.
Worse still, most of the people who are subjected to subpoena-based surveillance will probably never find out about it. That's because very few companies (kudos, Twitter!) inform their customers when law enforcement subpoenas their records. That means the only way you're likely to find out about such a subpoena is if you are arrested, tried in court, and the prosecution uses the subpoenaed records as evidence against you. Investigations that never lead to charges won't leave a public trace that any surveillance against you ever took place.
But it's even worse. If you do find out in time to try to quash the subpoena, a judge will probably cite the third party doctrine, which says you have no right to privacy in any information you hand over to a third party like a cell phone company, to kick you out of court.
And it's worse, yet. In most parts of the United States today, law enforcement can access the content of many of our communications by subpoena authority alone. That's because the Electronic Communications Privacy Act (ECPA), passed in 1986, puts a six month expiration date on the Fourth Amendment. Under the obsolete but active law, emails and text messages -- unlike the letter in your desk -- lose their warrant protection after 180 days.
It should tell us something very alarming that law enforcement submitted 10,801 subpoenas to US Cellular last year, and only 702 warrants. Our private information shouldn't be up for grabs to any prosecutor who wants it -- especially when we have no meaningful way to defend our information against improper or warrantless surveillance, and when the subpoena system is cloaked in secrecy. The subpoena standard creates a legal environment ripe for abuse.
Take action now to modernize the law.
Cross-posted from the ACLU of Massachusetts PrivacySOS blog.
Stay informed
Sign up to be the first to hear about how to take action.
By completing this form, I agree to receive occasional emails per the terms of the ACLU's privacy statement.
By completing this form, I agree to receive occasional emails per the terms of the ACLU's privacy statement.

